We can use the SPNego configuration wizard to enable authentication for all users belonging to a Active Directory to log on transparently to the AS Java with Single Sign-On.
- WebAS Java 640 SP15 or higher
- JDK 1.4 or higher
- Microsoft Windows Server 2000/2003 Active Directory
How to start the wizard:
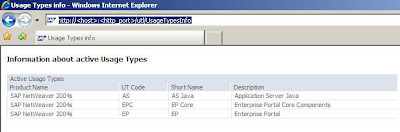
1) http://host:port/spnego
2) In the SAP NetWeaver Administrator by following the path System Management -> Configuration -> SPNEGO Configuration Wizard.
Steps:
1) Create and configure a service user on the Active Directory Servers (ADS), which act as a Kerberos Domain Controllers (KDC) with the below properties
- The password of the user must never expire.
- The user must be enabled to use DES encryption.
2) On the ADS for each Kerberos Realm, register with the ADS service user a Service Principal Name (SPN) for every DNS name that can be used to access the AS Java with Kerberos authentication.
- setspn -a HTTP/FQDN serviceusername
- setspn -a HTTP/hostname serviceusername
- Do a quick check with setspn -L to see the settings are succssful.
- setspn -L serviceusername
- You should get the below screen.
 3) LDAP settings in Configtool
3) LDAP settings in Configtool
- Logon to the Configtool and navigate to cluster-data -> UME LADAP data
- We have to connect j2ee UME to ADS. In order to do this, upload dataSourceConfiguration_ads_readonly_db_with_krb5.xml attached to the SAP Note 994791

- Enter the data in Connection details
- Make sure to test the connection and Test Authentication
- Restart the J2ee system.
4) Run SPNego wizard
- Start the SPNego wizard
- Select the check box Service user is created and configured in Active Directory to confirm that this step is completed
- Select the checkbox UME configuration includes SPNego specific settings to confirm that this step is completed
- Choose Next to proceed
- In the Jerberos Realm screen, Enter the name of the Kerberos Realm or Windows Domain inside the input field Realm Name.
- Choose Add KDC to add the host address and port for the Key Distribution Center (KDC).
- Choose Retrieve Principal to retrieve the AS Java Kerberos Principal Name (KPN), registered for the AS Java service user in the LDAP Directory.
a. Enter the Service User Name.
b. Enter the Service User Password.
- Choose Type Principal to manually enter the AS Java’s KPN.
a. Enter the KPN of the AS Java in Principal.
b. Enter the password for the AS Java service user in Password
- Choose Next to proceed
- Choose the Resolution Mode to use
- Use the Test resolution Mode functions to test the resolution of user ids from the configured domains
- Choose Next to proceed
- Choose the policy configuration to configure for Kerberos.
a. Choose Use existing to select an existing template for Kerberos.
b. Choose Create new to create a new policy configuration template.
- Add fallback authentication mechanisms for the case when Kerberos authentication fails.
a. Choose Enable Basic Password Fallback to enable the login modules for authenticating users with a user id and password as a fallback mechanism.
b. Choose Enable SSO with SAP Logon Tickets to enable the login modules for authenticating users with logon tickets as a fallback mechanism
- Choose Next to proceed
- Review the displayed information about the Kerberos configuration changes you made. The confirmation screen shows the configuration information for each of the configured Kerberos Realms or Windows Domains.
- Choose Finish to commit the changes. The wizard proceeds to the Final step and displays a confirmation of the changes you made.
- Restart J2ee system.
Final Steps:
- Logon to Visual Administrator and navigate to Server -> Services ->Security Provider, in Runtime -> Policy Configurations -> Components, select ticket.
- Switch to Edit mode and select spnego from Authentication template
- Select com.sun.security.jgss.accept from Components and choose Login Modul com.sun.security.auth.module.Krb5LoginModule
- Add isInitiator=false
- Change the Internet Explorer settings to use Integrated Windows authentication and test.
- Restart J2ee system.
TEST SSO:
Hit the URL http://host:port/irj/portal, It shoud not ask for username/password.


 3) LDAP settings in Configtool
3) LDAP settings in Configtool